

July 22, 2022
Preventing Invoice Fraud
Invoice fraud is a menace to finance professionals at companies of every size and in…
June 15, 2022
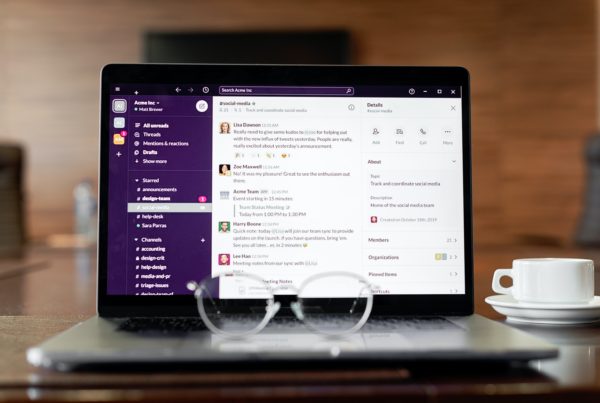
The Risks of Collaboration Tools
A majority of U.S. and global workers have come to rely on instant messaging and…

May 16, 2022
The Danger of Misconfigured APIs
As APIs become one of the most critical components of the software supply chain, misconfigured…

April 14, 2022
Russian Cyberattacks Quietly Thwarted by FBI
As the war in Ukraine continues, the United States remains under heightened threat of Russian…

March 16, 2022
Cyber Warfare and Insurance Coverage
Insurers, lawyers, and business owners have been debating the question of what constitutes cyber warfare…

January 18, 2022
Log4j Silver Lining
While Log4j has been nothing but a headache for the past five weeks, there may…

December 16, 2021
Many VPN Services Fall Short of Their Hype
Many widely used, popular VPN services fall short of their hype. A recent investigative analysis…

October 12, 2021
More WFH Dangers: Hackers Leverage In-Home Attacks
The high number of Americans working from home continues to present opportunities for hackers to…

September 17, 2021
Password Managers Are Safe: How Your Data is Protected in Password Management Apps
Password managers are safe, effective tools for thwarting cybercriminals in their non stop attempts to…
June 15, 2021
Your Mental Image of Cyber Crime Gangs is All Wrong
The way we think about cyber crime gangs is holding us back from truly addressing…



